By: Gamze Yurttutan
Published: June 01, 2022 | Updated: September 05, 2024
Read time: 5 minutes
The story goes that when President Nixon’s team fed military data into a computer to find out when they would win the Vietnam War, they were informed that they had already won five years earlier.
Although it’s a tale of dubious authenticity from a time when automated data analysis was in its infancy, reliable simulations are an important part of strategy. And that pertains as much to armed combat as to cybersecurity. But, unlike its military counterpart, cybersecurity simulations have largely been left languishing in the Nixon era. That’s to say, they’re still nonexistent for most businesses.
Now, that situation’s finally starting to change. And, to the chagrin of cybercriminals worldwide, technology is simulating possible cyberattacks before the actual perpetrators even get a chance.
Catching heat
It’s not a matter of ignorance that things are only changing now. The cost of building and coding replicas of business systems exclusively to host simulated breaches and attacks has been unaffordable for most businesses until recently.
The upside is that the availability of simulations to assist in cybersecurity testing coincides with recent improvements in cybersecurity risk assessment and management.
Our earlier article “Catching heat” discusses how to evolve to beat cybercrime by flexibly adjusting to changing threats and quantifying the risks. To avoid leaving such an approach out in the cold to fend for itself, businesses traditionally apply various kinds of testing:
- Vulnerability scanning relies on databases of known vulnerabilities to automatically detect system flaws
- Penetration testing, or “pentesting,” relies on individuals to identify known vulnerabilities and then exploit them
- Red teaming, borrowing Cold War terminology, relies on “red teams” to conduct scenario-based attacks on specific targets to assess mitigative responses by “blue teams”
But all these tests have shortcomings that can lead a cybersecurity solution that appears solid in theory to flail in reality. The automated nature of vulnerability scanning restricts it to a predefined repertoire of threats. The human involvement in pentesting and red teaming leaves them constrained by human biases and capabilities. As a result, none of the three approaches are able to stay fully on top of imminent threats. The tests are also conducted on live systems that need to be interrupted, so continuous analysis is not possible—even in the case of vulnerability scanning, which has limited human involvement.
It’s in the ability to better predict the nature of future attacks and remain permanently vigilant where simulations can help.
Simulating heat
A breach & attack simulation, such as Mastercard's Cyber Front, relies on replicas of business systems to simulate the actual threat landscape. Since it’s not conducted on actual systems, it can be run continuously without the need to wait for vulnerability scanning windows.
It also uses real threat samples and techniques culled from the live cybersecurity environment to keep up with imminent threats. The simulation can then test existing detection and response capabilities and provide precise mitigation guidance to address shortcomings.
When synched with one of the contextual and quantitative cybersecurity solutions discussed under “catching heat,” breach & attack simulations create a virtuous loop. The simulations provide enhanced data inputs to the cybersecurity solution, and the solution provides data inputs to the simulations to allow for better threat scoring. The main benefits of breach & attack simulations may be compared with the three traditional approaches to testing accordingly:
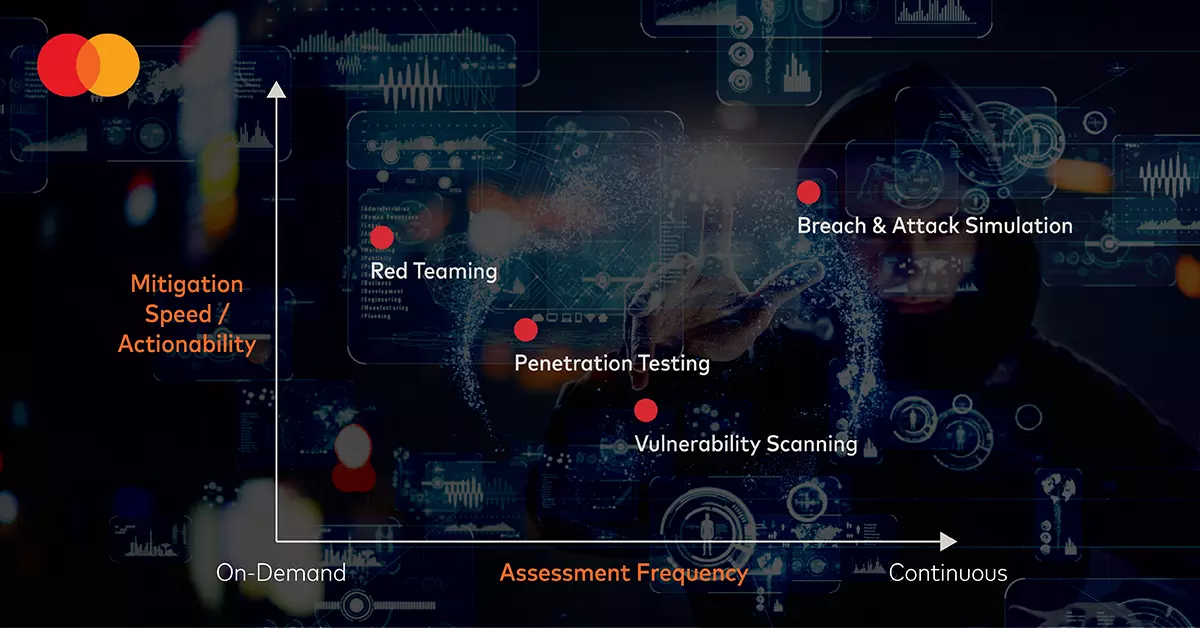
The position of breach & attack simulations in the top right corner shows it to be an improvement from traditional testing on both axes. And for many businesses, the entirely automated solution will be convenient, non-intrusive and affordable.
Nevertheless, for prominent businesses handling highly sensitive data, complete automation could theoretically bring some additional risk. In that regard, a cautionary tale remains from the Nixon story.
Breach & attack simulations are only as intelligent as the actual threat landscapes that inform them. And that doesn’t preclude humans from coming up with entirely novel ways to conduct cybercrime. Happily, most businesses aren’t in Nixon’s position of having to evaluate a risk to human life. Yet, just as Nixon could never have relied on a computer simulation to guide his strategy in Vietnam, no president today would put all their faith in one either. The degree of reliance would admittedly be different between the two eras, but the necessity for human involvement wouldn’t change.
So, for the riskiest of situations, where a marginal gain may still be worth the additional cost, occasional red teaming may still have a role. For all other situations, a continuous simulation of the most sophisticated cyberattacks will allow business to do more than keep step with cybercrime. Rather, they’ll be one step ahead of it.
Click here for more information on Mastercard’s Cyber Quant and Cyber Front solutions, combining a contextual and quantitative approach to cybersecurity with breach & attack simulations and optional red teaming.