By: Dan Pastor and Gamze Yurttutan
Published: September 30, 2022 | Updated: August 16, 2024
Read time: 10 minutes
- Table of contents
Introduction: A collective “us”
It is a scenario eerily reminiscent of recent times. When one body is put at risk, so is everybody in contact with it.
Being part of a resilient community can reduce that risk. In epidemiology, it is called “herd immunity.” In cybersecurity, third-party risk management (TPRM) is supposed to provide it. In the same way a disease peters out when it cannot contaminate enough people, a breach cannot spread when its surroundings are secure.
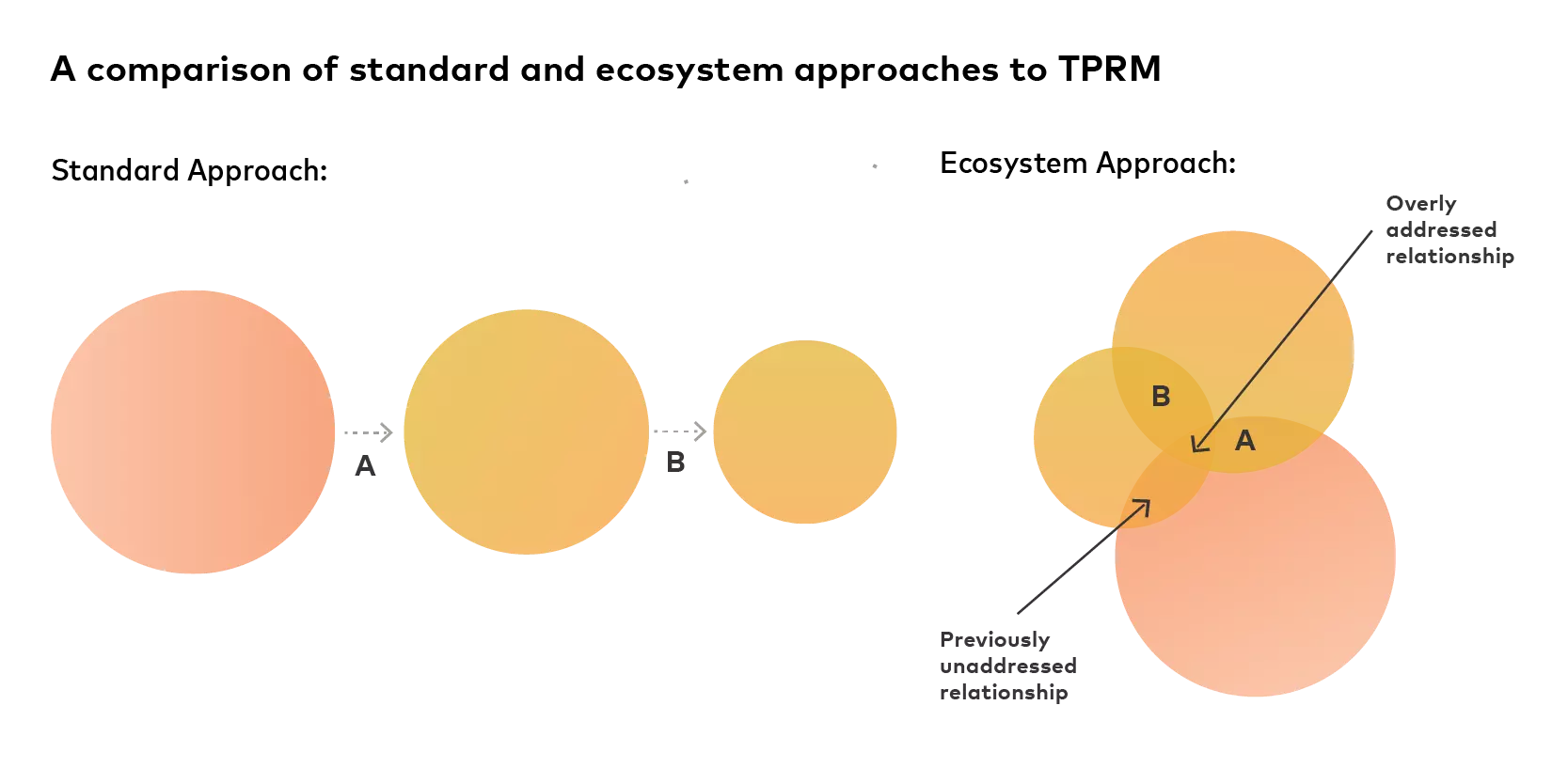
An ecosystem approach takes the “me versus them” mentality of standard TPRM and reorients it around a collective “us”
But the “me versus them” mentality of standard TPRM approaches makes that resilience difficult to achieve. Third parties tend to be an afterthought in cybersecurity; fourth parties and beyond tend to be ignored entirely.
Businesses often assume that third-party risk can be managed based on the amount of data shared or its sensitivity. That is not wholly misled, but it does ignore that a breach affecting some innocuous data can rapidly infect other areas. An ecosystem approach solves that by reorienting cybersecurity, and by extension TPRM, around a collective “us.”
This new approach to cyber resilience is timely. The average cost of a data breach is higher than ever at US$4.88 million worldwide in 2024, according to IBM. Third-party breaches were the third-biggest factor to increase that average cost after security system complexity and a shortage in security skills.
This report offers the following perspectives to address the problem:
- the status of TPRM in cybersecurity
- third-party value chains versus platform-based ecosystems
- balancing inherent risk with residual risk
- aspirational versus operational considerations
Cybersecurity versus TPRM: A distinction without a difference
The collective “us” behind an ecosystem approach to cybersecurity crosses an invisible line that separates businesses from their third parties. It is a line defined by perceived corporate boundaries in a boundaryless online world, and it goes back to when TPRM was emerging as something new and separate.
But the evolution of standard TPRM approaches from timely to anachronistic was fast.
Only 4% of business respondents to a recent survey by RiskRecon, a Mastercard company, state high confidence based on questionnaire responses that their third-party vendors are meeting security requirements. At the same time, twice as many businesses manage over 250 vendors in 2023 versus in 2020, according to the same survey.
Many individual businesses are at least on a better footing than a few years ago in terms of options.
- External threat landscape analyses provide insights into which actors pose ongoing or future risk and reasons.
- Quantitative self-assessments take traditional cybersecurity out of a reactive “space invaders” arcade-game mentality by keeping businesses one step ahead via quantified and centralized views of risk.
- True risk assessments of web presence combine the selection, assessment and monitoring of vendors with self-evaluations and industry benchmarking.
- Breach & attack simulations create virtuous loops by providing enhanced data inputs to quantitative cybersecurity solutions that in turn feed the simulations to allow for better threat scoring.
- Cyber crisis exercises prepare businesses for response readiness through interactive scenarios.
Yet it remains challenging for a business to assess which security issues of its third parties are most pressing. Asking a third party to conduct an internal self-assessment risks inherent bias if not supported by independent validation.
The problem is not so much the patronizing nature of many approaches — which can lead to difficult negotiations when one party considers another not up to snuff and so calls for additional financial investment — but the assumption that third parties cannot be trusted.
Only 4% of business respondents state high confidence that their third-party vendors are meeting security requirements
It also does not help that all third-party assessments, external or internal, tend to focus on the confidentiality of data rather than its integrity or availability in the traditional CIA triad.
Only the “C” is addressed because the “I” and the “A” are seen as issues for internal databases and system infrastructure that have little bearing on policies around third-party data sharing. But the “C” may as well stand for compliance as its main impetus, and the “I” and the “A” are now unavoidable with shared “as a service” or hosted “as a platform” offerings.
Third-party value chains versus platform-based ecosystems: Threads to webs
In the beginning were individual businesses. And those businesses created value chains that led to valuable products. Partnerships with third parties, and then third parties’ third parties, confused the chains that originally went directly from supplier to producer to distributor to consumer and back. Linear relationships were replaced by sprawling relationships extending in multiple directions.
Traditional cybersecurity is bottom up and largely internally focused. A business starts with its own data and examines it from the CIA perspective of confidentiality, integrity, and availability. If it has the budget or the inclination, it might also wonder about the data confidentiality in third-party relationships.
Partnerships with third parties, and then third parties’ third parties, confused the value chains
An ecosystem approach to cybersecurity is top-down and largely externally focused. A business looks at all the operators within its ecosystem to establish defined roles and objectives. It then examines the data that informs those practices across the ecosystem.
The ecosystem approach is dauntingly broad in scope. It works because it appreciates how businesses operate as platforms where multiple third parties exist in an ecosystem. In turn, those third parties also operate as platforms for other third parties to create other ecosystems. Further economies of scale occur where those ecosystems — some large, some small — partially overlap.
Nonetheless, the economies and efficiencies associated with an ecosystem do not negate the significant cost of cybersecurity. The risks within an ecosystem may be numerous; the negotiations between the parties on what should be covered by whom may be fractious. A solid business case is still needed to justify investment.
Inherent risk versus residual risk: The tech–compliance tradeoff
Businesses, particularly smaller ones, often face the dilemma of whether to remain competitive by investing in technology or to remain secure — and, by extension, compliant — by investing in cybersecurity.
Quantitative solutions can help alleviate staffing requirements for traditional manual approaches. But organizations with 5,000 or fewer employees saw increases in the average costs of data breaches in 2023: 13%, 21% and 20% for organizations with under 500, 500–1,000 and 1,001–5000 employees, according to IBM. By contrast, larger organizations saw slight decreases in average costs.
Different industries also face different challenges. Financial institutions might be a more common target for hackers than private healthcare providers, but the average total cost worldwide of a healthcare breach at US$9.77 million in 2024, according to IBM, dwarfs the financial sector at US$6.08 million. The value of health information might not be as immediately obvious as a credit-card number, but it cannot simply be canceled either.
There comes a point where marginal reductions in risk do not justify substantial increases in investment. Ultimately, it comes down to a balance between two choices:
A significant determinant in the balancing act is the risk appetite of a business. But that appetite should not be indulged with discrete lines connecting to third parties:
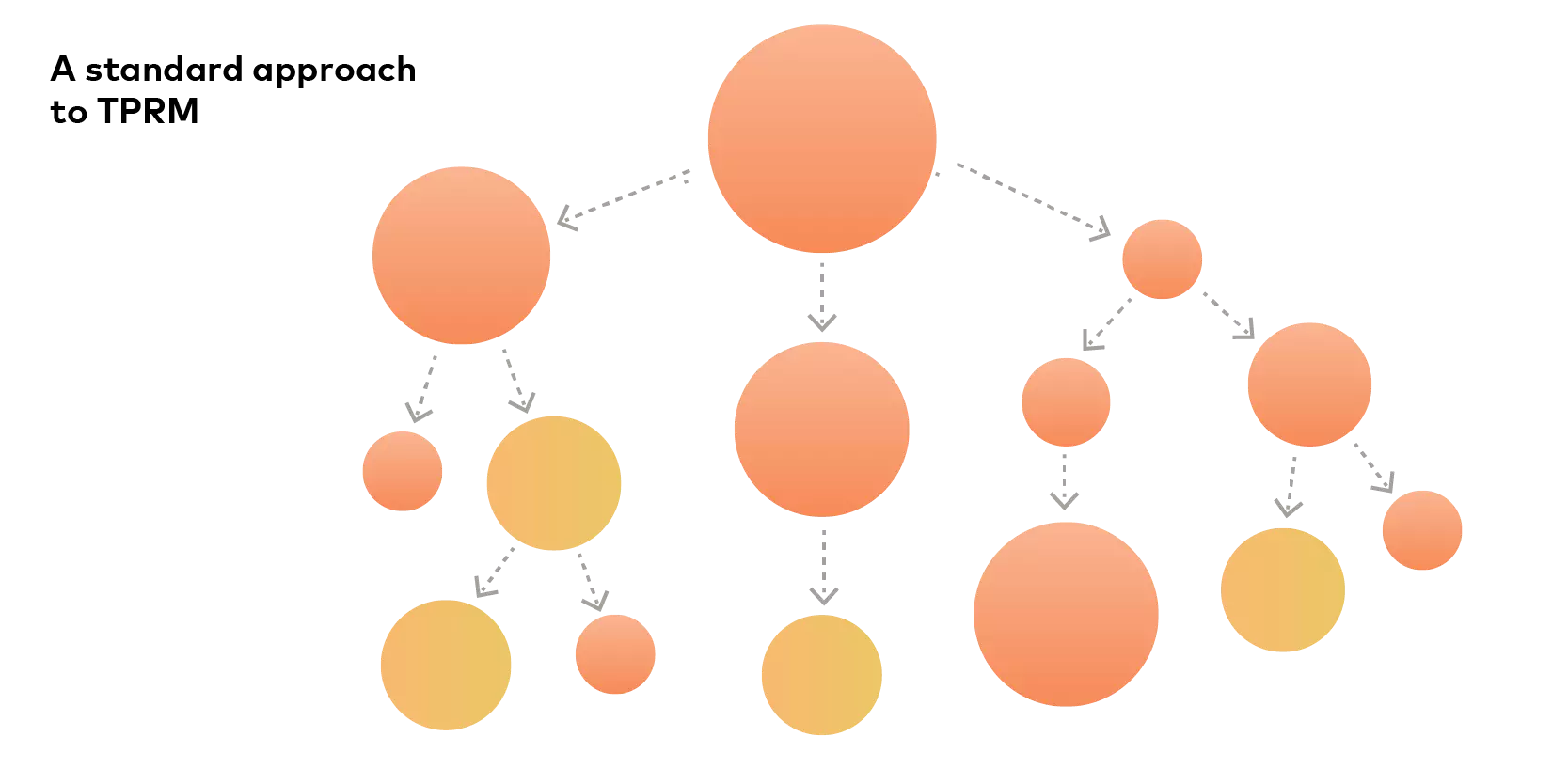
Rather, the appetite should be moderated by the best way to maximize efficiency and reduce redundancy in an ecosystem:
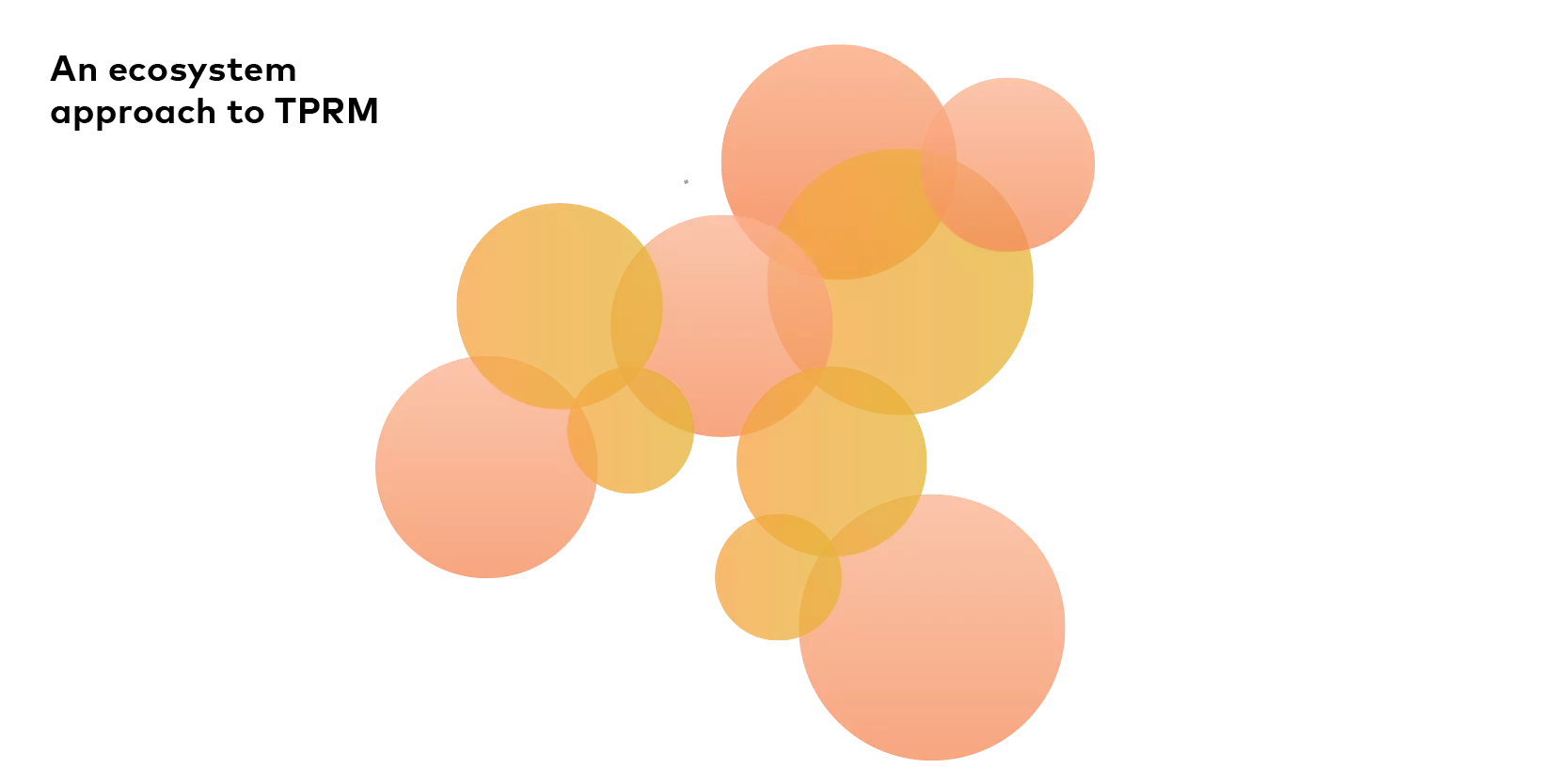
The relationships between businesses vary based on the amount of overlap between the circles and the depth of the shading. Multi-tiered assessments of risk across the coordinated ecosystem then allow businesses to allocate appropriate levels of attention to the different segments within their respective circles:
Aspirational versus operational considerations: Individual responsibility
The collective “us” of a platform-based ecosystem instead of a “me versus them” mentality is designed to create herd immunity and economies of scale. But collectivity can only work if all the participants take personal responsibility for their actions. For all businesses, that means following the same process — whether limited or extensive in scope — to define their respective ecosystems:
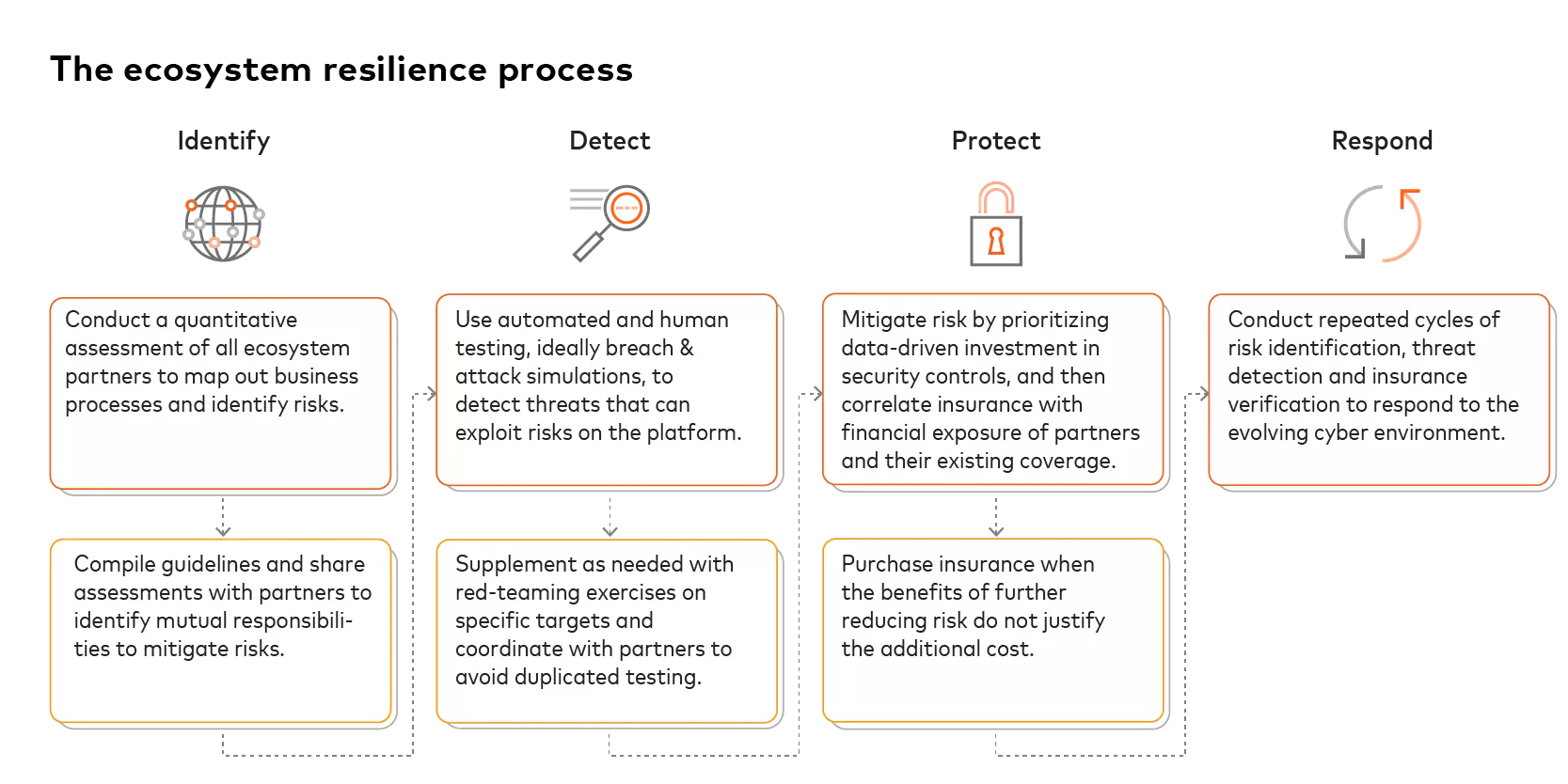
There is a communal, perhaps even utopian, ideal to the process. Ecosystem resiliency and financial efficiency improve as more businesses adopt a collective mindset. Better understandings of dependencies between businesses will help with cybersecurity negotiations — not in terms of one business gaining an upper hand over another but instead through a shared emphasis on expediency.
But introducing guidance to support this mass participation might seem obtuse when businesses are already struggling to comply with multiple regulations and frameworks. The challenge might seem particularly acute for businesses with sprawling global networks that span more than one jurisdiction.
Yet sprawl can also provide a good starting point for coordination, particularly when several third parties ultimately ladder up to the same umbrella organization.
- Case study
A multi-country conglomerate of banks, insurers and healthcare brands faces business interruption and financial losses caused by cyberattacks. A lack of awareness of which specific security gaps pose the greatest threats calls for a way to quantify risk and prioritize investment effectively.
The conglomerate implements a comprehensive and quantifiable risk assessment across all businesses and locations to calculate risk levels, maturity of controls and potential financial impacts. The results enable informed decision-making and support for new investment.
The deployment of 19 priorities for remediation over two years reduces the entire conglomerate’s risk level by 30%, representing savings of $24 million in potential losses.
An alternative to industrial conglomerates is industry consortiums. Their preexisting collaborative approaches can also provide natural starting points.
- Case study
Several major data breaches at home and in neighboring countries stimulate a country’s financial ecosystem to improve prevention and response capabilities nationwide.
The country’s main clearing house ramps up investment in cybersecurity, the 17 bank brands in the country’s banking association form a cybersecurity collective, and the financial sector’s computer security incident response team (CSIRT) incorporates services and solutions to bolster current capabilities.
A standard risk evaluation and quantification methodology helps establish a common framework to measure systemic risk across the whole ecosystem, which includes benchmarking against neighboring countries.
Based on the framework, the financial sector is preparing to run surface risk assessments, conduct breach & attack simulations and execute cyber crisis exercises to strengthen its security posture. The benefits should span the country’s financial service providers.
These starting points make ecosystem resilience less daunting. Still, they remain foundational as long as guidance around ecosystem resilience is directed exclusively at businesses. It should be equally — if not more — directed at the providers of cybersecurity solutions to businesses.
An analogy comes from the development of certain open finance frameworks that aim to do more than just expand the scope of open banking. A shared functionality takes independent connections between providers and recipients of open finance data and wraps them up in the consistent and efficient provision of connected products and services.
Governments, in partnership with industry bodies and harnessing the network security offered by payment networks, now need to apply that same collective mindset to cybersecurity.
The purpose of a framework is not to eliminate competition in the space, but rather to ensure that providers of cybersecurity solutions work with their customers to adhere to a collective standard. TPRM is notably the most challenging aspect of the European Union’s Digital Operational Resilience Act (DORA), according to a Mastercard-sponsored survey between November 2022 and February 2023.
Conclusion: A soft landing
Third-party relationships have transformed corporate monoliths into social butterflies. A traditional TPRM approach expects those butterflies to socially distance. That is a tall order.
A business cannot function properly and remain completely protected when its expectations of third parties are anything less than its expectations of itself. Nor can a business be expected to achieve those expectations when the available cybersecurity solutions do not adhere to a comprehensive provider-independent framework couched in a collective mindset.
Cybersecurity exists to toughen vulnerable components of individual businesses against breaches. Cyber resilience softens the impact of those breaches by taking a holistic view of all businesses in an ecosystem.
Unlike in epidemiology, vaccination is not a possibility in cybersecurity. But cybersecurity does still allow for herd immunity through a resilient approach that enables ecosystems — like societies — to contain an infection and rapidly rebound, recover and adapt.
Contact us to learn how Mastercard’s Cyber & Enterprise Risk practice supports the full ecosystem resilience cycle with Cyber Insights, Cyber Quant, RiskRecon, Cyber Front, and Cyber Crisis Management.